Custom Signals
Custom Signals allow teams to programmatically add organizational knowledge and context-specific insights to their changes. These signals capture tribal knowledge, compliance requirements, and team-specific deployment criteria that automated analysis might miss.
How to Submit Custom Signals
Submit Custom Signals using the Overmind CLI:
overmind changes submit-signal \
--title 'Environment' \
--description 'Change made in PROD' \
--value -2 \
--ticket-link "https://github.com/your-org/repo/pull/123"
Successful Output
When a Custom Signal is successfully submitted, you'll see output like this:
Successfully created signal for change 52b44273-77b2-447d-8ac8-61897ddfd9f0
{
"signal": {
"properties": {
"name": "'Test Signal'",
"value": 3.14,
"description": "This is a test signal submitted from the CLI",
"category": "Custom"
}
}
}
This confirms the signal was created and shows the unique change ID it was associated with.
You will then also be able to view the custom signal within the Overmind app and the associated PR comment.
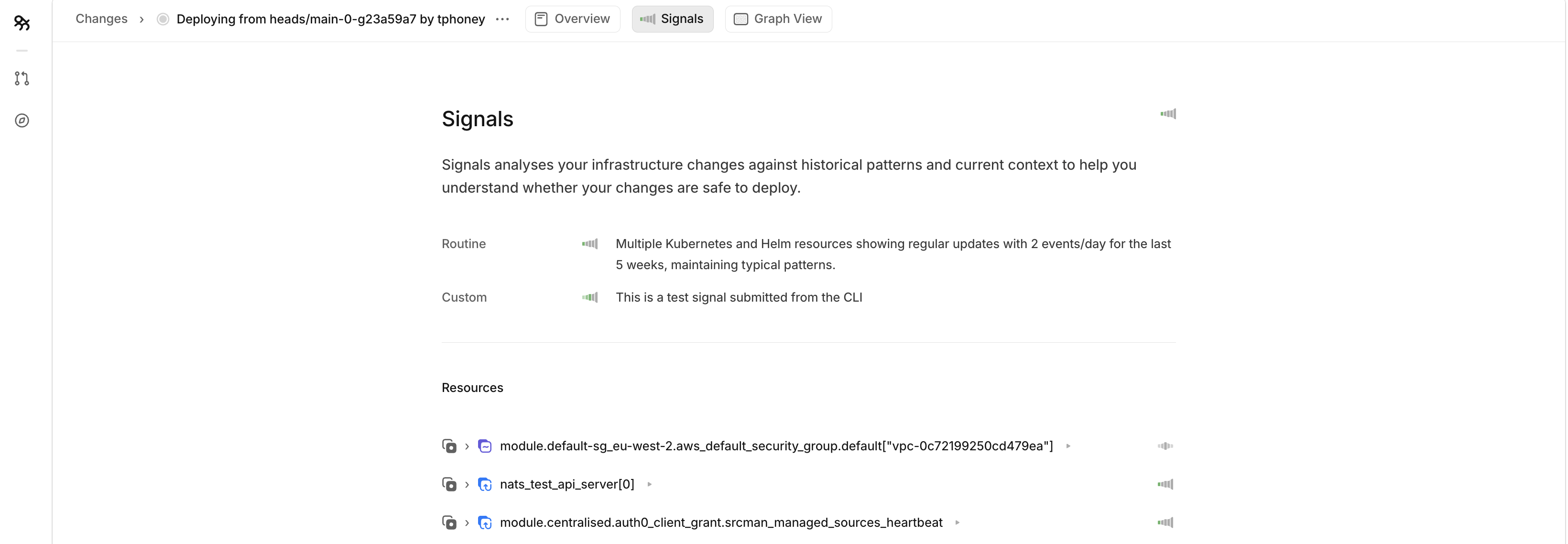
Parameters
--title: Signal name (e.g., "Environment", "Business Impact", "Compliance")--description: Explanatory context providing details about why this signal matters--value: Score from -5 to +5 indicating risk/confidence level--ticket-link: Reference to the change, PR, or ticket for traceability
Scoring Guidelines
- -5 to -3: High risk signals requiring careful review
- -2 to -1: Moderate risk signals needing attention
- 0: Neutral baseline with no special impact
- +1 to +2: Positive confidence indicators
- +3 to +5: High confidence signals supporting deployment
Common Use Cases
Environment Awareness
Flag deployments based on target environment:
# Production deployment
overmind changes submit-signal \
--title 'Environment' \
--description 'Change made in PROD' \
--value -2 \
--ticket-link "$PR_URL"
Business Timing Context
Consider deployment timing impact:
# Business hours deployment
overmind changes submit-signal \
--title 'Timing' \
--description 'Deployment during business hours' \
--value -1 \
--ticket-link "$PR_URL"
Compliance and Reviews
Track compliance requirements and approvals:
# Security review completed
overmind changes submit-signal \
--title 'Compliance' \
--description 'Security review completed and approved' \
--value +2 \
--ticket-link "$PR_URL"
Technical Context
Provide technical deployment context:
# Database migration
overmind changes submit-signal \
--title 'Migration' \
--description 'Database schema change requires manual review' \
--value -3 \
--ticket-link "$PR_URL"
CI/CD Integration
GitHub Actions
Integrate Custom Signals into your GitHub Actions workflows:
- name: Submit Environment Signal
run: |
if [[ "${{ github.head_ref }}" == *"prod"* ]]; then
overmind changes submit-signal \
--title 'Environment' \
--description 'Change targeting PROD environment' \
--value -2 \
--ticket-link "$ticket_link"
else
overmind changes submit-signal \
--title 'Environment' \
--description 'Change targeting non-PROD environment' \
--value 0 \
--ticket-link "$ticket_link"
fi
Dynamic Signal Generation
Create signals based on change analysis:
- name: Analyze Changes and Submit Signals
run: |
# Check for database migrations
if git diff --name-only HEAD~1 | grep -q "migrations/"; then
overmind changes submit-signal \
--title 'Migration' \
--description 'Database migration detected - requires DBA review' \
--value -3 \
--uuid c8a0bd61-372f-4ba9-b649-6a535b70060e
fi
# Check for security-related changes
if git diff --name-only HEAD~1 | grep -E "(auth|security|iam)"; then
overmind changes submit-signal \
--title 'Security' \
--description 'Security-related files modified' \
--value -2 \
--uuid c8a0bd61-372f-4ba9-b649-6a535b70060e
fi
Best Practices
Signal Design
- Use consistent titles across your organization
- Provide descriptive context in signal descriptions
- Score based on actual risk rather than arbitrary values
- Reference relevant tickets or PRs for traceability
Team Implementation
- Define standard signal categories for your organization
- Create CI/CD templates that submit relevant custom signals
- Document signal scoring criteria for consistency
- Monitor signal effectiveness and adjust scoring over time
Troubleshooting
Signal not appearing:
- Verify the change ID exists before submitting signals
- Check that the ticket-link matches the change being analyzed
- Ensure CLI authentication is working properly
Incorrect scoring:
- Review your scoring guidelines with the team
- Consider if the signal category matches the intended purpose
- Validate that the risk level aligns with actual deployment impact
For additional support, visit our support documentation or join our Discord community.